· Puttarak Khwan · Programming · Security · Tools · 3 min read
Scan code with Credential Scanner on Azure DevOps
Introduce the sample way to scan the credential expose via Credential Scanner on Azure DevOps

🥳 Happy New Year 2023! 🥳
Wishing everyone a great year ahead!
Now, let’s get down to business. Today, I’m going to introduce you to a handy tool that checks for leaked passwords, secrets, certificates, or any sensitive content in your source code or configuration files.
Introducing our hero, “Credential Scanner” (affectionately known as CredScan), developed by Microsoft. It performs scans for sensitive data that developers might accidentally include in the source code during Continuous Integration (CI) runs on the Azure DevOps Pipeline, ensuring that our source code becomes more secure.
Prerequisites:
- This tool is available only on the Azure DevOps Build System.
- You need to have the Microsoft Security Code Analysis Extension installed in your organization’s account.
How to set up:
Open your Project in Azure DevOps Account.
Choose the Pipelines menu.
- For a new pipeline: Select “New” -> Source code -> Repository -> Configure Pipeline.
- For editing an existing pipeline: Click on “Edit” for the pipeline you want to modify.
This will open a window showing the YAML file. Then, click on “Show assistant” on the top right-hand side.
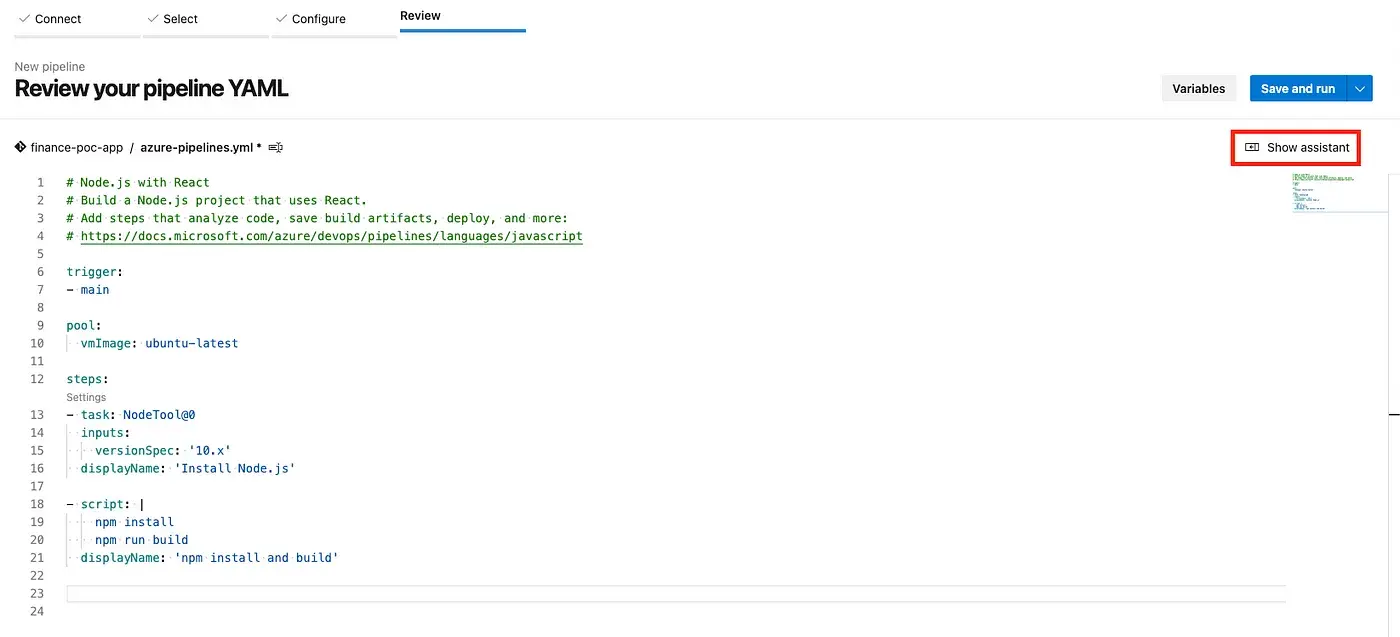
Type the name of our hero in the Search box and click to add it to our YAML.
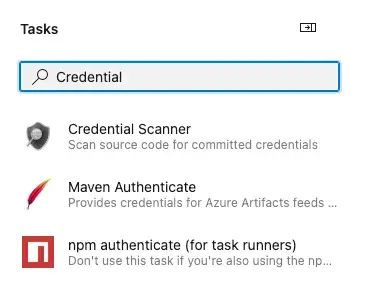 Type “Credential Scanner” in the Tasks box.
Type “Credential Scanner” in the Tasks box.
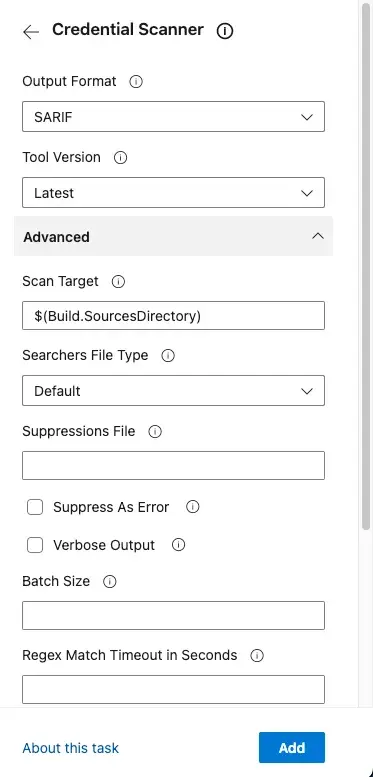 You can customize the configuration of the CredScan tool.
You can customize the configuration of the CredScan tool.
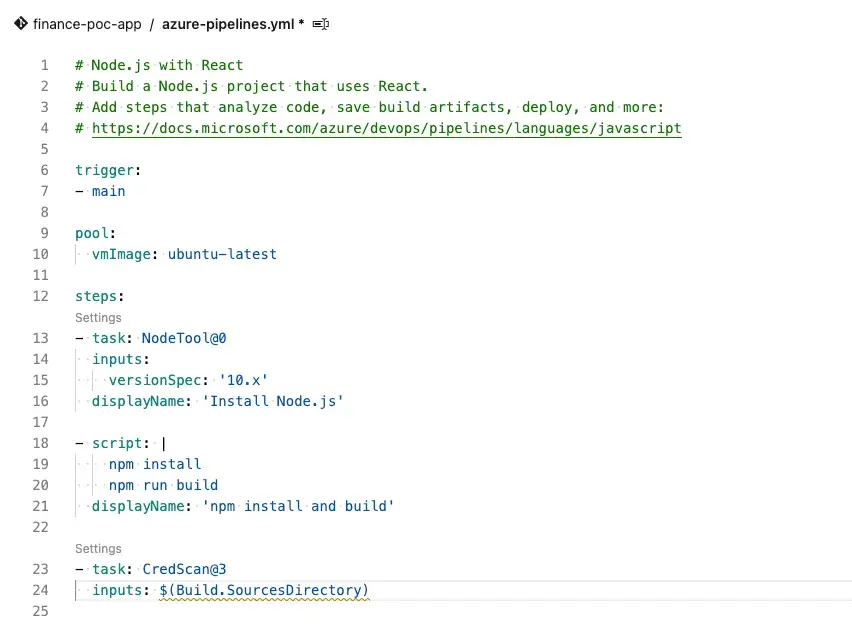 The Credential Scanner tool has been successfully added to our Pipeline.
The Credential Scanner tool has been successfully added to our Pipeline.
- After that, you can click on Save YAML.
From now on, every time the Pipeline is run, it will scan for sensitive data and display points where there are passwords, secrets, certificates, and other sensitive information for us to see.
Let’s take a look at the actual results from the scan using the Credential Scanner tool:
After running the scan in my project, I found that there are leaked keys of certificates from a library used in the project. 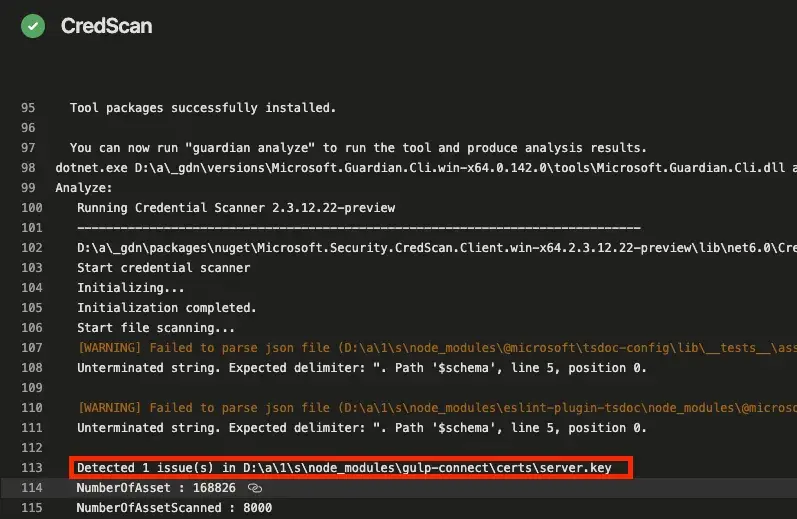
Do we have any leftover sensitive data? 🥲 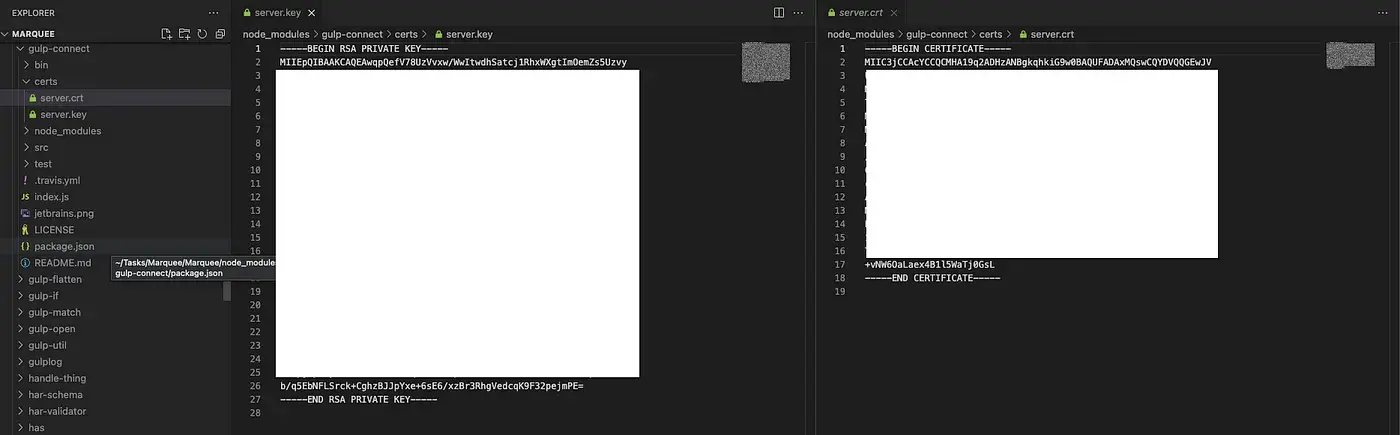
In this situation, it’s essential to investigate further and verify if the keys are indeed exposed. I suggest checking and verifying carefully if the sensitive information is still accessible. It might be a cause for concern. 🥲
Once you identify any potential issues or mistakes in your source code, I strongly advise you to address them promptly. As a software engineer, keeping the code secure is essential, and swift action can help prevent any possible security breaches. 🧑🏻🔧 (P.S. Keep it hush-hush; we don’t want others to know about it yet 😂)
P.S. Lastly, if anyone is interested in reading more about the technology of Mycos Company, you can follow and read further content on their Medium page at https://medium.com/mycostech
References: